Category Archives: SAML
VMware Cloud Director and Google IdP SAML Config
Posted by vmknowledge
VMware Cloud Director do not have built-in OTP support but each organization can use SAML 2FA/MFA purpose.
Yestarday with my two friends Kemal Tek and Arif Alpagut made a test for see how SAML configuration could done by Google as an Identitiy Provider.
SAML provides a solution to allow your identity provider and service providers to exist separately from each other, which centralizes user management and provides access to SaaS solutions.
When a user logs into a SAML enabled application, the service provider requests authorization from the appropriate identity provider. The identity provider authenticates the user’s credentials and then returns the authorization for the user to the service provider, and the user is now able to use the application.
In this article VMware Cloud Director is SAML enabled application, Google is identity provider (IdP).
Many IdP out there for example Azure could be if you wonder SAML flow, check it below.

Lets configure SAML for our VMware Cloud Director tenant which name is Aren-Tenant1-Corlu
Let login to tenant portal, go to Administration tab, from Identitiy Provider section choose SAML and click CONFIGURE.
Not : From GUI if its one time configured there no option to clear everything, only thing is disable identity provider.
Give an uniq name for Entity ID you will use this on IdP site, you can also retrive the metadata to use it when configure custom SAML App at Google.
For example you will use url below for redirection from google which is ACS URL (Assertion Consumer Service), check the md:AssertionConsumerService section in metadata file
https://vcdtekcor01.dorukcloud.com/login/org/aren-tenant1-corlu/saml/SSO/alias/vcd

Login to your Google Admin Console and go to Apps > Web and Mobile Apps section and add an custom SAML app.

Set app name , desc and picture …

Use option 1 and download metadata

Set ACS,Entity ID, Start URL and Named ID like below ( be carefull about spaces when you copy/paste 😀 ) Named ID format will be EMAIL, leave the Named ID Basic Information > Primary Email.
if you wonder what is Named ID ; SAML 2.0 name identifier formats control how the users at identity providers are mapped to users at service providers during single sign-on. Security Access Manager supports the following name identifier formats: Email address.

You can see some articles add different attributes but i did not, actually with SAML also we can get some values from IdPs.

Then it will looks like below ….

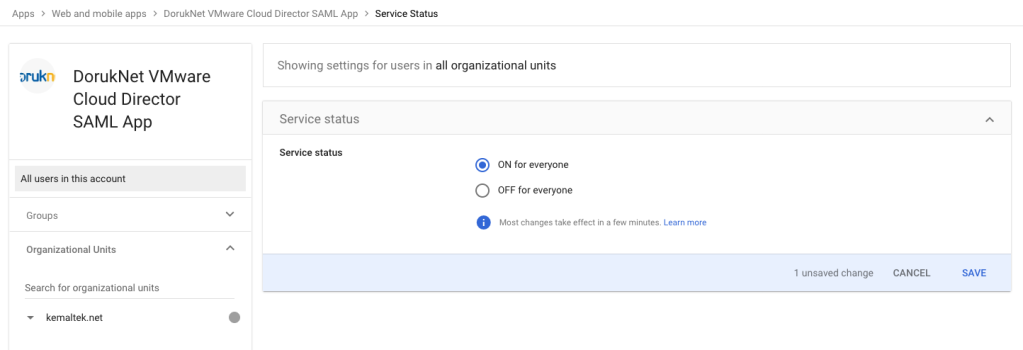
Then enable for your users in your organisation to access this custom SAML app. Over the mouse on OFF for everyone and click on it then select ON for everyone.
*I’m not google expert just only allow access to related user to use such app.
Lets back to VMware Cloud Director, upload Google Metadata, import google user as a SAML user.
From Identity Provider tab activate it and upload the metadata which is downloaded from Google. The picture below there is a button REPLACE METADATA XML FILE becuase this is second time i’m configuring SAML with Google.
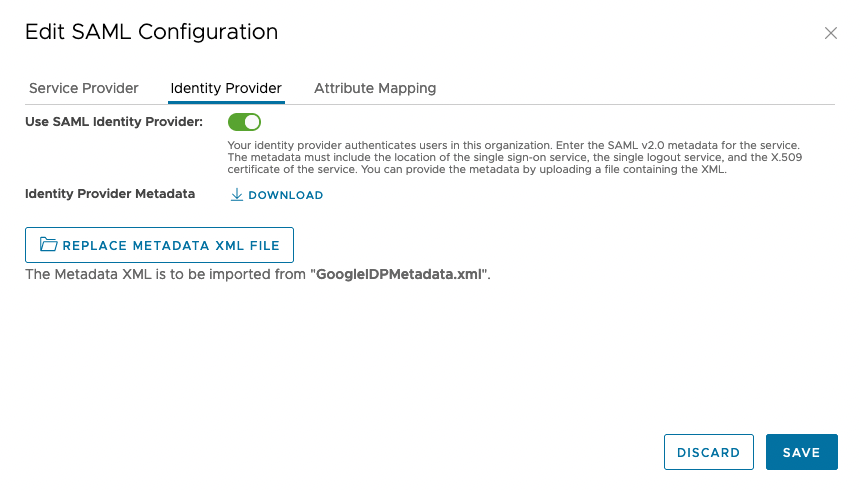
Then IdP become active.

Now time to import user, go to Administration tab, from Access Control click Users then Import Users and type your organisation user email address.

Try to login VMware Cloud Director with tenant url, you will see additional option SIGN IN WITH SINGLE SIGN-ON and then standard google authontication process will start, you can auth via email, google app what google IdP offer you …

You can see that on the up right corner you are logged with your google account.

*Note sometimes when you made some changes on google about settings somehow you are getting “Error: app_not_configured_for_user” or like that , clear the cache or wait little then everything start to work again. Never give up 😀
Thats it !
Posted in SAML, VMware Cloud Director 10.4
Tags: 2Fa, AUTH, authorization, IdP, MFA, SAML, SAML enabled application, VMware Cloud Director